Cybercriminals will do anything they can to get what they want. They will lie and cheat to break into an organization’s network and siphon off the data or gain control. One of the most utilized tactics that cybercriminals use today is called social engineering. This month, we will discuss social engineering and how it puts everything you work for in jeopardy.
- Register
- Login
CoreTech Blog
Cloud computing has become a massive benefit for modern businesses, but every company has unique needs that require tailored technology solutions. A one-size-fits-all approach can be detrimental and leave you wasting money or worse—not getting the value out of your investments. In this month's newsletter, we offer five key tips for effectively deploying cloud services in your business.
Generating and capitalizing on digital leads is crucial for business success. A well-thought-out strategy to attract leads through websites, emails, and social media can significantly enhance a company's ability to create a good customer experience and grow its business. This month, we’ll examine this element of a business and give you a step-by-step guide to getting the most out of your digital marketing efforts.
Most businesses rely on their technology. However, a failure to manage that technology can lead to significant financial waste and operational inefficiencies. One major way a business can waste money is through over-investment in unnecessary or overly complex IT infrastructure. Let’s briefly examine how companies waste their money on technology and how to identify if technology is working for your business.
One of the worst things that can happen to any organization is to be infiltrated with ransomware. Ransomware is a strain of malware that allows hackers to lock down files or computing systems and then ransom access back to the organization. It can really be a problem.
Emerging technologies offer significant opportunities for businesses to achieve their goals. However, understanding how and when to leverage these technologies is crucial. One of the most rapidly advancing technologies today is artificial intelligence (AI). Yet, AI encompasses more than what one might initially think. Many of the most impactful business tools are powered by a branch of AI called machine learning (ML). This month's newsletter delves into machine learning, its mechanics, and its applications within a business context.
Big data is now a crucial resource for businesses of all sizes, including small enterprises. Today, businesses have unprecedented access to vast amounts of data, enabling them to make more informed decisions and operate more efficiently. This month’s newsletter explores how small businesses harness big data's power.
Technology is a major part of today’s business. It’s fair to say anyone that works in business today is at least semi-proficient with the technology needed to complete their tasks. Unfortunately, for many people, however, the fact that their business requires complicated technology is problematic. This is because at any given moment there are people looking to undermine their job, seeking access to accounts that will allow them to siphon money and data from organizations.
Every organization deals with operational problems in one manner or another. There are dozens of situations that can cause downtime, and having a comprehensive data backup plan can alleviate many of them. This month’s newsletter discusses business continuity and how data backup is a critical piece of that process.
Businesses need a certain degree of good fortune to continue to grow in the manner in which they project when they hang out their shingle. With so many businesses failing after a very short time, taking advantage of the opportunities you’re given is extremely important. In this month’s newsletter, we’ll go through some of the things that a business can do to take better advantage of some opportunities.
The modern customer is more educated than ever before. As a result, you have to have an active strategy to build great customer experiences so you can retain business with them. In this month’s newsletter, we’ll go over some things you can do to improve your customer relationships.
Phishing is one of the most prevalent issues individuals and businesses must confront when operating online. This is because there are literally billions of these scam attempts sent each day. That’s right, billions. With over a hundred billion scam attempts sent every year, your business is already getting phished, it’s just a matter of time before someone falls for it.
Remote employees are in a conundrum when it comes to data security. While you might be able to protect data stored locally on your company’s in-house network, securing data in use by employees while out of the office is another matter entirely. How can you guarantee that your business is protecting its data and other sensitive resources from prying eyes?
How often does your business find that it’s struggling with new technology implementation, either on the software side of the house or on the hardware side? Have you considered that the cloud provides powerful solutions to your business’ woes in the form of virtualization? With the right resources at your disposal, you can use virtualization to create incredible opportunities to improve operations for your business and make it more secure and flexible in the process.
Encryption stands as a formidable shield for businesses, fortifying their security architecture. While often discussed in VPN contexts, its significance in securing email solutions cannot be overstated. Why is email encryption indispensable for businesses of all sizes? Let's explore.
The cloud has become a go-to resource when businesses are trying to find and consistently depend on digital tools that otherwise would be out of their price range. One cloud issue that isn’t often mentioned in the course of choosing computing resources is cloud waste. Cloud waste refers to the inefficient or unnecessary consumption of cloud computing resources, leading to higher costs without delivering corresponding value. This month, we will look at some of the impacts of cloud waste and how to avoid it as much as possible.
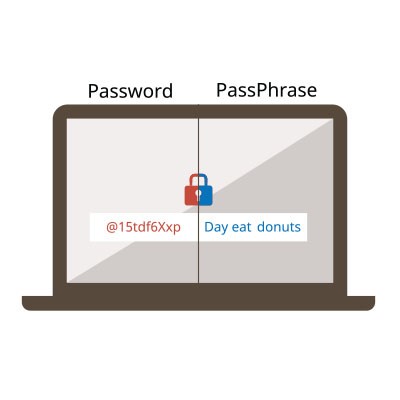
Securing your accounts against unauthorized access begins with the implementation of a strong password. It's crucial to recognize that not all passwords offer the same level of protection. Here are five essential guidelines to ensure the security of your accounts.
You often hear about “drives” when working with technology, but there are many different types that a computer might use in your business's day-to-day operations. Today, we want to explain what some of these drives do and why you should know where they are and what they stand for.
Safeguarding your business' infrastructure from various threats is a well-known imperative. In discussions about network security, the term "endpoint" frequently arises. Exploring the significance of securing all endpoints is the focus of today's article.
Technology is an essential component for most businesses. Strategic integration of technology has been proven to address significant operational challenges that often elude smaller businesses and startups. In this context, we'll explore three critical questions about business technology that every tech-savvy individual should be acquainted with and make clear the importance of such knowledge.
Mobile? Grab this Article!
- You are here:
- Home /
- Newsletter Content